Breaking News
Main Menu
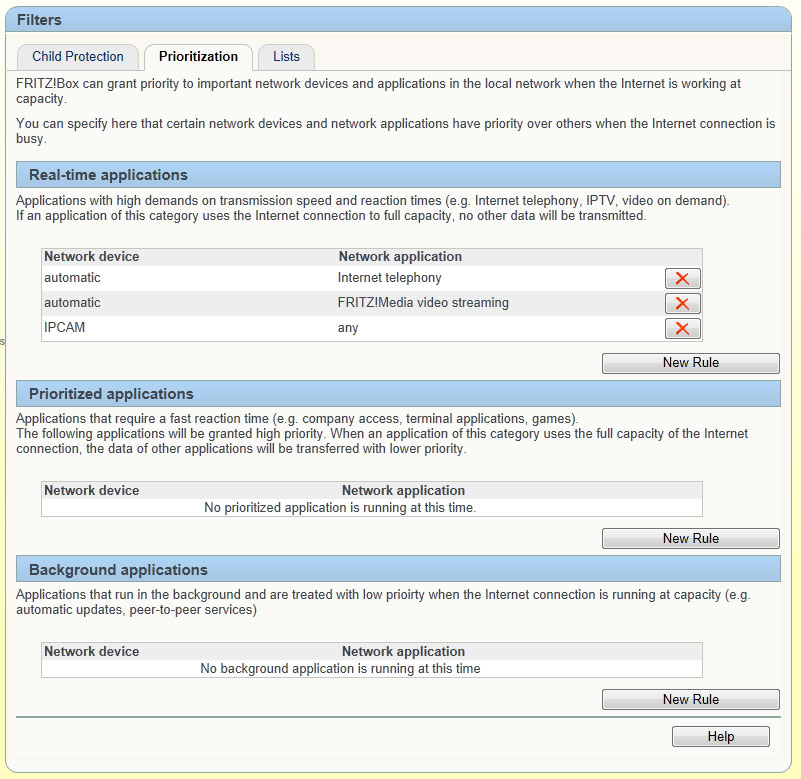
Fritz Box 7360 Password Hack
суббота 06 апреля admin 57
• Click the 'Forgot your password?' • Click the 'Send Push Service Mail' button. If the button is not displayed, the 'forgot password' push service is not configured. • Call up the email with the same device you used to request the push service mail and follow the instructions in the email. If you did not receive an email, either the the email account information entered for the push service is not correct, or the FRITZ!Box is not connected to the internet. Important:The email may have been classified as unsolicited advertising (spam).
Your FRITZ!Box 7360 and describes ports, buttons and LEDs. 1.1 FRITZ!Box at a Glance Access to the Internet The FRITZ!Box connects multiple computers fast and safely with the Internet. Other network-compatible devices like smartphones and game consoles can use the FRITZ!Box for their Internet connection.
Bertazzoni serial number location. In this case, also check the spam folder of your email inbox.
I hacked my Fritz!Box (yeah, a bad name for a german router) and I'm entirely sure that it has a backdoor integrated too. That's why I wiped and flashed it with an alternative image. That and the Telecom's Speedport router are the most popular routers by far in Germany. And both have backdoors, I know that other router manufacturers also integrate backdoors from a source who works at such a company. A friend can also verify the fact, because a different employee told him the same. Also it's public that the ISP can upgrade, modify, flash and disable features remotely. My friend's router has wifi, but their provider disabled it remotely within the firmware (it even has an antenna) and his ISP wants him to pay 5€/m to re-enable wifi.
I really wonder why nobody complained about that earlier. Also the interesting thing here is that for a very long time, you weren't allowed to use a different router than the one provided by your ISP. Which enforced their surveillance monopoly. Here's an article about reverse engineering the backdoor in D-Link routers using IDA: PoC Available. This is probably NOT a backdoor. Most likely your ISP is using a technique like TR-069.
This enables them to push settings for voip/TV, and in your friends case wifi. A lot of DSL providers are starting to use this for less intrusive (?) goals like measuring noise and attenuation at the clients end once a day, so they can adjust the speed accordingly. AVM is a very nice company and you should not accuse them without proof. They actually provide an option to disable TR-069 in the page 'Provider Services' ('Allow automatic configuration by the service provider' and 'Allow automatic updates'). If you don't have this option you could try installing the original firmware from avm.de. Maybe you are still able to flash the modem with the original firmware from, and configure it yourself?
>> 'you can easily install other firmware' That's what I did, I flashed it with a custom firmware (that was after I got aware of the backdoor). I've not 'reverse-engineered' the base image of my own router like in the article above, because that's a lot of work.
I've worked on an awful lot of routers, hubs, switches of all sorts, enterprise and consumer. Have been network administrator for a large global company and I think that I can trust my sources. What the new user 'blablablaat ' mentioned is obvious, I'm not stupid to make something like this up.
Of course I have no 'Provider Services' or anything remotely similar enabled, but it's still possible to connect to the router and take control over it according to my source and I've seen it back then, when I asked for him/her to show it. Now why, do you expect me to prove that? A security researcher, is more qualified than me to create the convincing report you're asking for, sorry. You can feel free to do it yourself too, if you want. It's not my intention to spread rumors or FUD, but to make you at least aware of that your router ain't secure.
